Introduction:
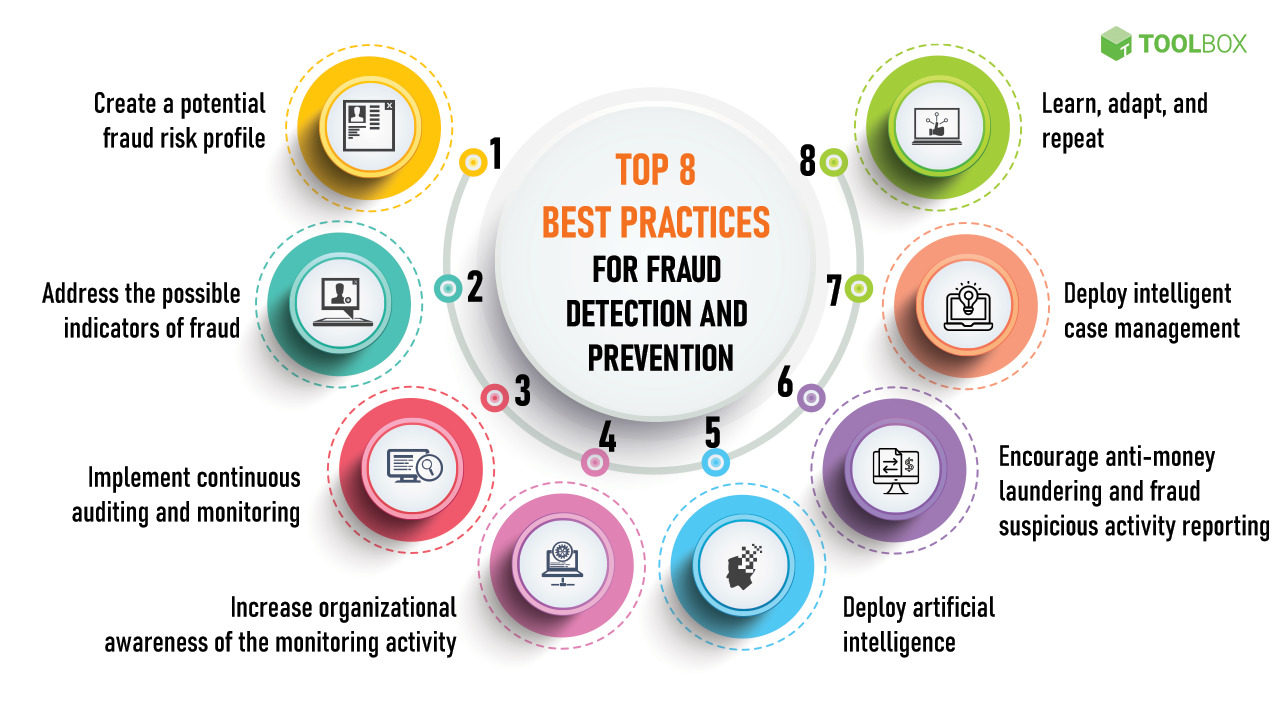
In today’s digital landscape, financial fraud poses a significant threat to businesses of all sizes. From unauthorized access and data breaches to money laundering and payment scams, the potential for losses and reputational damage is substantial. To effectively safeguard your organization, implementing a robust methodology for detecting fraudulent financial transactions is crucial. This guide delves into key strategies and best practices to help you build a strong line of defense.
Methodology:
-
Data Collection and Monitoring:
- Gather comprehensive transaction data: Securely acquire and store detailed information on all financial transactions, including timestamps, amounts, merchants, locations, and user IDs.
- Implement real-time monitoring: Establish systems that continuously analyze transactions for suspicious activity, such as unusual patterns, deviations from baselines, or inconsistencies with user profiles.
- Leverage transaction enrichment: Enhance data with additional context like IP addresses, device fingerprints, and geolocation to paint a more holistic picture.
-
Rule-Based Detection:
- Define clear rules and thresholds: Establish specific criteria for flagging potentially fraudulent transactions based on industry standards, historical data, and risk assessments.
- Customize rules based on user profiles and behavior: Tailor rules to individual users or groups to account for expected variations and reduce false positives.
- Continuously update rules: Regularly revise rules to adapt to evolving fraud tactics and maintain effectiveness.
-
Machine Learning and Anomaly Detection:
- Train machine learning models: Develop algorithms that can learn from historical transaction data and identify anomalies deviating from normal patterns.
- Utilize unsupervised learning: Employ techniques like clustering and outlier detection to uncover hidden patterns and suspicious activities.
- Fine-tune models and analyze results: Continuously refine models and interpret results to ensure accuracy and avoid false positives.
-
Authentication and Authorization:
- Enforce strong authentication: Implement multi-factor authentication (MFA) and other secure access controls to verify user identities before authorizing transactions.
- Implement authorization rules: Define clear permissions for different user roles to restrict access and prevent unauthorized activities.
- Monitor user behavior: Track login attempts, device usage, and other user activity for potential signs of compromise or suspicious behavior.
-
Investigation and Response:
- Establish a clear escalation process: Define a well-defined procedure for investigating flagged transactions, involving risk management, security teams, and potentially law enforcement.
- Gather evidence and document findings: Collect detailed information about the flagged transaction, user, and other relevant context for further analysis and potential remediation.
- Block or reverse fraudulent transactions: Take immediate action to prevent losses, such as blocking unauthorized access, reversing fraudulent transactions, and reporting incidents to authorities.
Additional Considerations:
- Stay informed: Keep abreast of emerging fraud trends, tactics, and vulnerabilities through industry publications, security conferences, and collaboration with other organizations.
- Invest in employee training: Regularly educate employees on security best practices, phishing awareness, and how to report suspicious activity.
- Conduct regular audits: Periodically review your fraud detection systems, assess their effectiveness, and identify areas for improvement.
- Seek expert assistance: Consider consulting with security professionals or specialized vendors for tailored solutions and guidance.
Example:
Imagine you run an e-commerce store and implement a combination of rule-based and anomaly detection techniques. A rule might flag transactions exceeding a certain amount without prior authorization, while your ML model might identify unusual purchase patterns from a new user logging in from an unfamiliar location. These alerts would trigger an investigation, potentially uncovering attempted credit card fraud.
Conclusion:
By adopting a multi-layered approach that combines data monitoring, rule-based detection, machine learning, robust authentication, and swift response, you can significantly bolster your defenses against financial fraud. Remember, vigilance, continuous improvement, and proactive measures are key to safeguarding your business and its financial well-being in the ever-evolving threat landscape.